The popular image of online dangers is scary bad guys trying to steal our stuff. This image is accurate if you remember to include unfettered corporate interests as the scary bad guys.
Our protections against our good friends the telcos and cable companies have never been strong, and now they’re nearly non-existent. Repealing Broadband Privacy Rules, Congress Sides with the Cable and Telephone Industry sums it up beautifully: “Internet providers will be given new powers to harvest your personal information in extraordinarily creepy ways.” And buy and sell it with no oversight or accountability, and law enforcement will get their hands on it as surely as road apples draw flies.
What can we do about it? I believe that the best solution is legislative. I prefer technical solutions for protecting ourselves from hostile and predatory interests, but there aren’t many, and they’re incomplete. Internet access is a requirement for many routine aspects of our daily lives, and even if you avoid going online you have no knowledge or control of the information the vendors and service providers that you use are collecting and trading, or what people share about you on social media. Stores, electric and gas utilities, healthcare providers, tradespeople, private clubs, non-profit organizations, charitable groups, banks, insurance companies, and on and on. They all collect information about you, and many trade it freely. Of course, it’s not fair to assume that everyone is venal, but even when a vendor has a heart of gold they may be lacking in technical competence.
Don’t hold your breath waiting for meaningful laws to protect us. What can you do? You can secure your online communications and your web surfing to a degree with Tails, the forgetful Linux distribution. We’ll get back to this after a brief rant about “helpful” web browsers.
“Helpful” Web Browsers
The good nerds behind Firefox and Chrome try so hard to help us, and the harder they try the more annoying they become. First there were the nice discreet little color-coded padlocks in the URL bar (Figure 1).
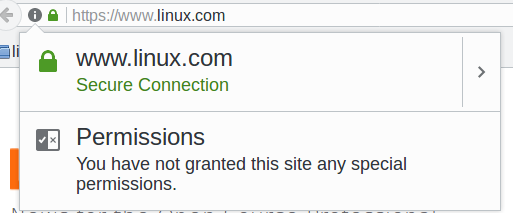
I like those. They don’t get in the way, and they tell useful information. Useful, that is, if you have any idea what it all means. And even if you do, how do you know you can rely on it? Root certificate authorities have been hacked multiple times, including bigwigs Verisign and Microsoft.
Then Firefox and Chrome got downright hysterical, and make us jump through multiple hoops to enter sites they think are dangerous. Sometimes these warnings are useful, for example when a site is infected with malware, or has been hijacked. Most of the time they’re simply not SSL-enabled, and then we see something like Figure 2.
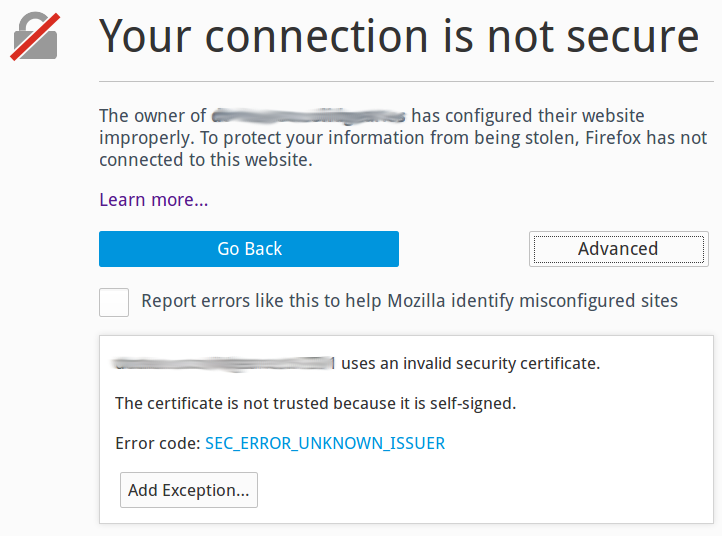
I appreciate the effort, but there is already excessive noise in normal computer use, and we are continually swatting away unhelpful notifications and warnings like annoying gnats. Many of these SSL defects are technicalities, like the domain name is not exactly correct. It’s all nutty anyway, because most of us are not security experts and have no idea how to evaluate if these warnings are meaningful.
Hide Yourself With Tails
Tails, the Amnesic Incognito Live System, is a nice live Linux distro that runs from removable media, like a USB stick, SD card, or DVD. Tails bundles a number of privacy tools into a polished Debian-based distro, including Tor (the Onion Router), HTTPS Everywhere, tools for controlling what information the Iceweasel web browser retains, NoScript, and other useful privacy tools.
To use Tails simply boot your Tails media. All the apps bundled in Tails are configured to route your traffic through Tor: email, Web surfing, instant messaging, the works. Tor foils traffic analysis by routing your online sessions through relays all over the world to hide your physical location, and to separate your identity from your online activities. Foiling traffic analysis is a substantial benefit, because marketers and government snoops rely on sophisticated traffic analysis to connect your identity to your online activities. You might have noticed how smartphones apps are especially greedy for your physical location; use the Tails Android app, Orbot. There is not a Tails app for iOS, but there is a Tor app for iOS.
Tor encrypts your session and hides your backtrail inside the Tor network of routers. After it leaves an exit node it’s back to whatever state it was when it left your computer, so if you’re surfing in the clear then it comes out in the clear. Encrypting your online sessions end-to-end is a separate problem, and Tails comes with a full complement of encryption tools: HTTP Everywhere to force SSL on sites that use SSL, OpenPGP for encrypting and digitally signing emails and documents, LUKS for disk encryption, OTR for instant messaging, and Nautilus Wipe for secure file deletion.
Tails leaves no trace; it makes no changes to the host system. When you’re finished reboot and it’s as though you were never there. If you need persistent storage you can copy files to a USB stick, or enable persistent storage on your Tails USB stick or SD card.
The downside of Tails is that Tor is often slow. For us fortunate ones, this is an inconvenience. For many people, it is a small price to pay for a literal life-saver.
Another hurdle is downloading and installing it onto removable media, which is an easy task when you know how. Fortunately the good Tails people have written a top-quality howto that walks you through every step, and provides excellent copy-and-paste commands, so that even a novice should be able to set it up.
Trust?
In preparation for this article, I followed the Tails installation instructions and created a brand-new Tails USB stick. You might notice the same thing I did: It still comes down to trusting unknown people, the Debian maintainers, the maintainers of the Tails downloads, various distro maintainers, the GPG signing keys, the Tails web site… we still have to place our trust in somebody.
Additional Reading
- UEFI Secure Boot: Big Hassle, Questionable Benefit
- Schneier on Security
- Electronic Frontier Foundation
Learn more about Linux through the free “Introduction to Linux” course from The Linux Foundation and edX.





