Artificial intelligence (AI) is not sci-fi anymore; machines have made their way into our lives with ever-increasing importance. Today, humans are teaching machines and machines already affect the way we live, make choices, and get entertained.
There are many ways we already use AI in our everyday lives:
* We ask our devices to perform simple searching tasks, play music, or send messages without touching them.
* We are overwhelmed with sometimes creepy suggestions of things we “want” to buy or lists of movies we will enjoy watching according to some smart algorithms.
* We’re already used to the idea of self-driving cars.
* And we can’t ignore the convenience of the new auto-fill and follow-up Gmail features.
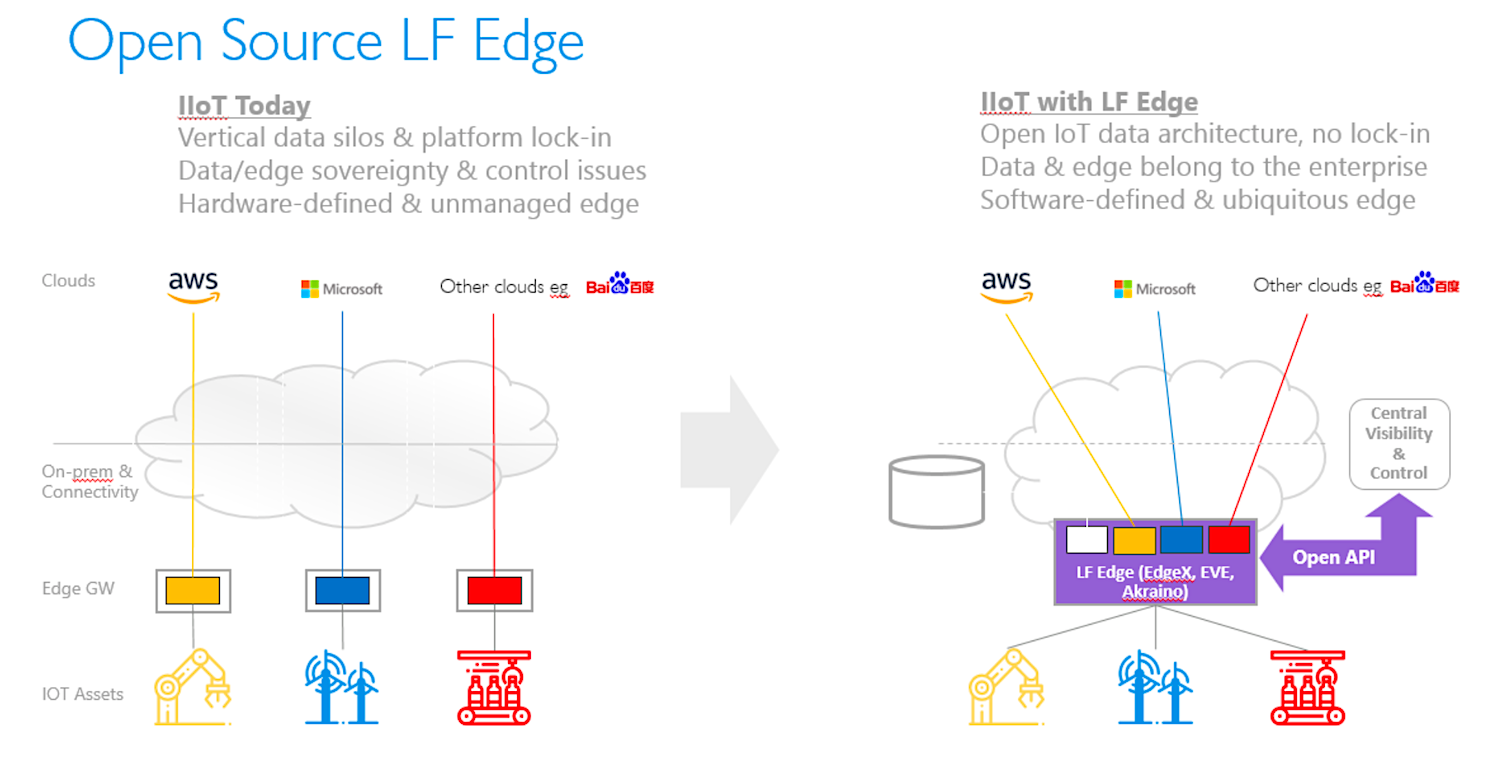
Machine Learning on Code
As AI technology matures and the number of use cases grows, you would think that developers would already be using machine learning to automate some aspects of the software development lifecycle. However, Machine Learning on Code is actually a field of research that is just starting to materialize into enterprise products. One of the pioneers of movement is a company called source{d}, which is building a series of open source projects turning code into actionable data and training machine learning models to help developers respect technical guidelines.
With every company quickly becoming a software company, intangible assets such as code represent a larger share of their market value. Therefore companies should strive to understand their codebase through meaningful analytic reports to inform engineering decisions and develop a competitive advantage for the business.
On one hand, managers can use tools like the open source source{d} engine to easily retrieve and analyze all their Git repositories via a friendly SQL API. They can run it from any Unix system, and it will automatically parse their companies’ source code in a language-agnostic way to identify trends and measure progress made on key digital transformation initiatives.
For example, as an engineering manager, you can track the evolution of your software portfolio. You can easily see what programming languages, open source or proprietary frameworks are becoming more popular as part of your development process. With that extra visibility, it becomes a whole lot easier to decide who to hire and develop a set of company-wide best practices
On the other hand, developers can save an incredible chunk of time by training bots to review their code as they submit pull requests (PRs). Once enabled across a large set of repositories, this could automate part of the code review process and enable developers to ship secure and qualitative code faster than ever before.
At the moment it checks for common mistakes, makes sure the style and format of each commits is consistent with the existing code base or highlights hotspots that might need closer attention. That’s huge already and clearly can benefit not only developers but companies as well. Imagine how much time and resources you could save from delegating your code review to a bot capable of working 24/7.
Assisted or automated code review is not the only Machine Learning on Code use case. In the coming years, machine learning will be used to automate quality assurance and testing, as well as bug prediction or hardware performance. For now, you can try source{d} Lookout and install it on your repository. It will listen for PRs, run analyzers and comment results directly on GitHub.
This article was produced in partnership with Holberton School.