Learn how to use the host_list and Nmap plugins to build inventory files for your Ansible playbooks.
Read More at Enable Sysadmin
Learn how to use the host_list and Nmap plugins to build inventory files for your Ansible playbooks.
Read More at Enable Sysadmin
Learn how to install, view, and query data in MySQL and its open source implementation, MariaDB.
Read More at Enable Sysadmin
Register for the ELISA Spring Workshop on April 5-7 to Learn More
SAN FRANCISCO – March 23, 2022 – Today, the ELISA (Enabling Linux in Safety Applications) Project, an open source initiative that aims to create a shared set of tools and processes to help companies build and certify Linux-based safety-critical applications and systems, announced a stronger ecosystem focused on automotive use cases with the addition of the Automotive Intelligence and Control of China (AICC), LOTUS Cars and ZTE.
“The ELISA ecosystem continues to grow globally with strong support from automakers across Asia and Europe,” Kate Stewart, Vice President of Dependable Embedded Systems at The Linux Foundation. “By leveraging the expertise of current and new ELISA Project members, we are defining the best practices for use of Linux in the automobiles of the future. “
Linux is used in all major industries because it can enable faster time to market for new features and take advantage of the quality of the code development processes. Launched in February 2019 by the Linux Foundation, ELISA works with Linux kernel and safety communities to agree on what should be considered when Linux is to be used in safety-critical systems. The project has several dedicated working groups that focus on providing resources for System integrators to apply and use to analyze qualitatively and quantitatively on their systems.
The Automotive Working Group discusses the conditions and prerequisites the automotive sector needs to integrate Linux into a safety critical system. The group, which includes collaboration from ADIT, Arm, Codethink, Evidence (a part of Huawei), Red Hat and Toyota, focuses on actual use cases from the Automotive domain to derive the technical requirements to the kernel as a basis for investigation within the Architecture Workgroup and to serve as a blueprint for actual projects in the future. There is also close collaboration with Automotive Grade Linux, which results in a meta-ELISA layer enhancing the instrument cluster demo for safety relevant parts. As leaders in the automotive industry, AICC, LOTUS Cars and ZTE will most likely join the Automotive Working Group.
New Global Automotive Expertise
As the industry’s leading ICV computing infrastructure company, AICC is committed to providing OEMs with intelligent vehicle computing platforms and digital bases for empowering them the differentiated application development ability. In November 2021, AICC released iVBB2.0 series products, which takes ICVOS as the core product, then develops ICVHW, ICVSEC, ICVEC, and other product units. Currently, iVBB2.0 has been delivered to many OEMs and achieved collaboration on cross-platform development, co-built SDV, multi-chip distributed deployment, data security policy deployment and car cloud collaborative computing.
“Becoming a member of the ELISA Project, is in line with the high real-time, high-security, and high-reliability commitment that AICC has always made,” said Dr. Jin Shang, CEO & CTO of AICC. “This will provide a guarantee for the mass production development of AICC’s ICV computing infrastructure platform from security and quality perspectives. Based on the elements, tools, and processes shared by ELISA, AICC will build safety-critical applications and systems relating to Linux requirements, leading to widely used and internationally influential products.”
LOTUS Cars, which was honored as “Manufacturer of the Year” at the News UK Motor Awards in 2021, is focused on the safety of intelligent driving. It is a world-famous manufacturer of sports cars and racing cars noted for their light weight and fine handling characteristics.
“Functional safety is critical to intelligent driving,” said Jie Deng, LOTUS Cars In-Vehicle Operating System Lead. “LOTUS focuses on ‘track-level intelligent drive‘ and is committed to ensuring that drivers stay away from risks through active redundancy of software and hardware. We are very excited to join the ELISA Project and work with industry experts to productize Linux-based safety-critical systems for more drivers to experience intelligent driving in a highly safe and fun way.”
ZTE Corporation is a global leader in telecommunications and information technology. Founded in 1985, the company has been committed to providing innovative technologies and integrated solutions for operators, government and consumers from over 160 countries. ZTE has established 11 state-of-the-art global R&D centers and 5 intelligent manufacturing bases.
Relying on key technologies and core capabilities in the communications field, ZTE Automotive Electronics is committed to becoming a digital vehicle infrastructure capability provider and an independent high-performance partner in China, facilitating the intelligent and networked development in the automobile field. ZTE has been dedicated to GoldenOS R&D for more than 20 years. On this basis, ZTE proposes the integrated automotive operating system solution of high-performance embedded Linux and high security microkernel OS/Hypervisor, covering all scenarios of intelligent vehicle control, intelligent driving, intelligent cockpit and intelligent network connectivities.
These new members join ADIT, AISIN AW CO., Arm, Automotive Grade Linux, Banma, BMW Car IT GmbH, Codethink, Elektrobit, Horizon Robotics, Huawei Technologies, Intel, Toyota, Kuka, Linuxtronix. Mentor, NVIDIA, SUSE, Suzuki, Wind River, OTH Regensburg and Toyota.
The Spring Workshop
ELISA Project members will come together for its quarterly Spring Workshop on April 5-7 to learn about the latest developments, working group updates, share best practices and collaborate to drive rapid innovation across the industry. Hosted online, this workshop is free and open to the public. Details and registration information can be found here.
Workshop highlights include:
A keynote by Robert Martin, Senior Principal Engineer at MITRE Corporation, about “Software Supply Chain Integrity Transparency & Trustworthiness and Related Community Efforts.” The presentation will discuss the capabilities emerging across industry and government to assess and address the challenges to providing trustworthy software supplies with assurance of integrity and transparency to their composition, source, and veracity – the building blocks of software supply chains we can gain justifiable confidence in at scale and speed.A session by Christopher Temple, Lead Safety & Reliability Systems Architect at Arm Germany GmbH, and Paul Albertella, Consultant at Codethink, about “Mixed-Criticality Processing on Linux.” This talk will help create a common understanding of mixed-criticality processing on Linux and the related problems, collect and discuss alternatives for addressing the problems.A discussion led by Philipp Ahmann, Business Development Manager at Robert Bosch GmbH, about a new Industrial IoT (IIoT) Working Group within ELISA. The open forum will allow the community to discuss framing lightweight SOUP safety standards, but focusing on those touch points which are not fully covered by other use case driven working groups.
Speakers include thought leaders from ADIT GmbH, Arm, Bosch GmbH, Bytedance, Codethink, Huawei, Mobileye, The Linux Foundation, MITRE Corporation and Red Hat. Check out the schedule and register to attend the workshop today.
For more information about ELISA, visit https://elisa.tech/.
About The Linux Foundation
The Linux Foundation is the organization of choice for the world’s top developers and companies to build ecosystems that accelerate open technology development and commercial adoption. Together with the worldwide open source community, it is solving the hardest technology problems by creating the largest shared technology investment in history. Founded in 2000, The Linux Foundation today provides tools, training and events to scale any open source project, which together deliver an economic impact not achievable by any one company. More information can be found at www.linuxfoundation.org.
The Linux Foundation has registered trademarks and uses trademarks. For a list of trademarks of The Linux Foundation, please see its trademark usage page: www.linuxfoundation.org/trademark-usage. Linux is a registered trademark of Linus Torvalds.
###
The post The ELISA Project Strengthens its Focus on Automotive Use Cases with Expertise from New Members Automotive Intelligence and Control of China, LOTUS Cars and ZTE appeared first on Linux Foundation.
Using Global Transaction Identifiers for data replication makes rollouts, debugging, and configuration much easier for admins.
Read More at Enable Sysadmin
Using Global Transaction Identifiers for data replication makes rollouts, debugging, and configuration much easier for admins.
Read More at Enable Sysadmin
RHACS monitors runtime data on containers to help you uncover potential vulnerabilities during product testing.
Read More at Enable Sysadmin
Some great insight into how a kernel sta
Click to Read More at Oracle Linux Kernel Development
How to get started with scripting in Python
Image
WOCinTech Chat, CC BY 2.0
Learn to use functions, classes, loops, and more in your Python scripts to simplify common sysadmin tasks.
Posted:
March 30, 2022
|
by
Peter Gervase (Red Hat, Sudoer), Bart Zhang (Red Hat)
Topics:
Programming
Python
Read the full article on redhat.com
Read More at Enable Sysadmin
Why it makes sense to write Kubernetes webhooks in Golang
When to choose Golang versus Python and YAML for writing Kubernetes webbooks.
lseelye
Mon, 3/21/2022 at 10:16pm
Image
Photo by Rachel Claire from Pexels
Towards the end of 2019, OpenShift Dedicated site reliability engineers (SREs) on the SRE-Platform (SREP) team had a problem ahead of a new feature release: Kubernetes role-based authentication controls (RBAC) wasn’t working. Or, rather, it wasn’t working for us.
Topics:
Kubernetes
Programming
OpenShift
Read More at Enable Sysadmin
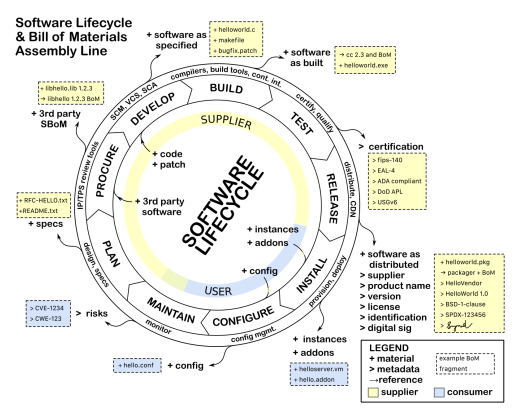
A software bill of materials (SBOM) is a way of summarizing key facts about the software on a system. At the heart of it, it describes the set of software components and the dependency relationships between these components that are connected together to make up a system.
Modern software today consists of modular components that get reused in different configurations. Components can consist of open source libraries, source code or other external, third-party developed software. This reuse lets innovation of new functionality flourish, especially as a large percentage of those components being connected together to form a system may be open source. Each of these components may have different limitations, support infrastructure, and quality levels. Some components may be obsolete versions with known defects or vulnerabilities. When software runs a critical safety system, such as life support, traffic control, fire suppression, chemical application, etc., being able to have full transparency about what software is part of a system is an essential first step for being able to do effective analysis for safety claims.
When a system has functionality incorporated that could have serious consequences in terms of a person’s well being or significant loss, the details matter. The level of transparency and traceability may need to be at different levels of details based on the seriousness of the consequences.
Source: NTIA’s Survey of Existing SBOM Formats and Standards
Safety Standards, and the claims necessarily made against them, come in a variety of different forms. The safety standards themselves mostly vary according to the industry that they target: Automotive uses ISO 26262, Aviation uses DO 178C for software and DO 254 for hardware, Industrial uses IEC 61508 or ISO 13849, Agriculture uses ISO 25119, and so on. From a software perspective, all of these standards work from the same premise that the full details of all software is known: The software should be developed according to a software quality perspective, with additional measures added for safety. In some instances these additional safety measures come in the form of a software FMEA (Failure Modes and Effects Analysis), but in all of them, there are specific code coverage metrics to demonstrate that as much of the code as possible has been tested and that the code complies with the requirements.
Another item that all safety standards have in common is the expectation that the system configuration is going to be managed as part of any product release. Configuration management (CM) is an inherent expectation in software already, but with safety this becomes even more crucial because of the need to track exactly what the configuration of a system (and its software) is if there is a subsequent incident in the field while the system is being used. From a software perspective, this means we need several things:
The goal, then, is to be able to rebuild exactly what the executable or binary was at the time of release.
From the above, it is inherently obvious how the SBOM fits into the need for CM. The safety standards CM requirements, from a source code and configuration standpoint, are greatly simplified by following an effective SBOM process. An SBOM supports capturing the details of what is in a specific release and supports determining what went wrong if a failure occurs.
Because software often relies upon reusable software components written by someone other than the author of the main system/application, the safety standards also have a specific expectation and a given set of criteria for software that you end up including in your final product. This can be something as simple as a library of run-time functions as we might expect to see from a run-time library, to something as extensive as a middleware that manages communication between components. While the safety standards do not always require that the included software be developed in accordance with a safety standard, there are still expectations that you can prove that the software was developed at least in compliance with a quality management framework such that you can demonstrate that the software fulfills its requirements. This is still predicated on the condition that you know all of the details about the software component and that it fulfills its intended purpose.
The included software components can be from:
Regardless of the source or current usage of the software, the SBOM should describe all of the included software in the release.
To this end, the safety standards expect that the following is available for each software component included in your project:
At a minimum, the SBOM describes the software component, supplier and version number, with an enumeration of the included dependent components. This is what is being called for in the minimum viable definition of an SBOM to support cyber security[1] or safety critical software[2].
Having a minimum level of information, while better than nothing, is not sufficient for the level of analysis that safety claims expect. Knowing exactly which source files were included in the build is a better starting point. Even better still is knowing the configuration options that were used to create the image (and be able to reproduce it), and being able to check via some form of integrity check (like a hash) that the built components haven’t changed is going to be key to having a sound foundation for the safety case. SBOMs need to scale from the minimum, to the level of detail necessary to satisfy the safety analysis.
While SBOM tooling may not be able to populate all of this information today, the tools are continuing to evolve so that the facts necessary to support safety analysis can be made available. An international open SBOM standard, like SPDX[3] can become the baseline for modern configuration management and effective documentation of safety critical systems.
[1] The Minimum Elements For a Software Bill of Materials (SBOM) from NTIA
[2] ISO 26262:2018, Part 8, Clause 12 – Qualification of Software Components
[3] ISO/IEC 5962:2021 – Information technology — SPDX® Specification V2.2.1
Peter Brink, Functional Safety Engineering Leader, kVA by UL, Underwriters Laboratories (UL)
Kate Stewart, VP Dependable Embedded Systems, The Linux Foundation