Although the Linux kernel is a highly secure layer in the ecosystem, the same cannot be said of every application that runs atop it. You might have an in-house application that has not been vetted for security (yet must be used), you might have found an app on a third-party download site, or you might be running applications on a machine that must retain the highest level of security. To that end, what do you do?
One thing that is available with Linux is the ability to sandbox applications. Sandboxing is an approach to running untrusted applications by limiting the environment in which they run. The app is run inside the “sandbox,” where it is provided a tightly controlled set of resources for the guest application to use.
Sound complicated? Believe it or not, there’s a piece of software available that makes sandboxing quite simple on Linux. The app is called Firejail and serves as an SUID (Set owner User ID upon execution) that reduces the risks of security breaches. Firejail can sandbox any type of process, be it a server or desktop application. It includes security profiles for a vast number of Linux applications and allows you to create your own, app-specific, profiles.
There is even a GUI application for Firejail, called Firetools, that offers system tray launcher for sandboxed apps; sandbox editing, management, and statistics. NOTE: The Firetools system tray integration may not work with every desktop environment.
With that said, I’ll show how to install and use both Firejail and Firetools.
Installing the Software
I will be demonstrating the installation of Firejail and Firetools on Ubuntu GNOME 16.04. This process should work fine on any Ubuntu-based distribution. To install the applications on another distribution, you will have to make minor modifications to the steps (such as using dnf as opposed to apt-get).
First, let’s install Firejail. Because the software is found in the standard repositories, installation is very simple. Follow these steps:
-
Open up a terminal window
-
Issue the command sudo apt-get install firejail
-
Type your sudo password and hit Enter
-
If prompted, type y to allow the installation to continue
-
Allow the installation to complete
Now let’s install Firetools. You won’t find this app in the standard repositories. However, the developer has made official .debs available. To install one of the .deb files, follow these steps:
-
Download the file associated with your architecture (either 32- or 64-bit)
-
Open a terminal window
-
Change into the Downloads directory with the command cd ~/Downloads
-
Issue the command sudo dpkg -i firetools*.deb
-
Type your sudo password and hit Enter
-
Allow the installation to complete
The installation very well may error out with dependency issues. If that’s the case, enter the command sudo apt-get install -f, to resolve the dependencies, and Firetools will be ready to use.
Using Firejail
Let’s first work with the Firejail command line. The developers have made it incredibly easy to use. Say, for example, you want to run Firefox within a Firejail. To do this, open up a terminal and issue the command firejail firefox. When you run the application, you will see that Firejail has initiated the child process and Firefox will open—running within its own sandbox (Figure 1).
How simple is that?
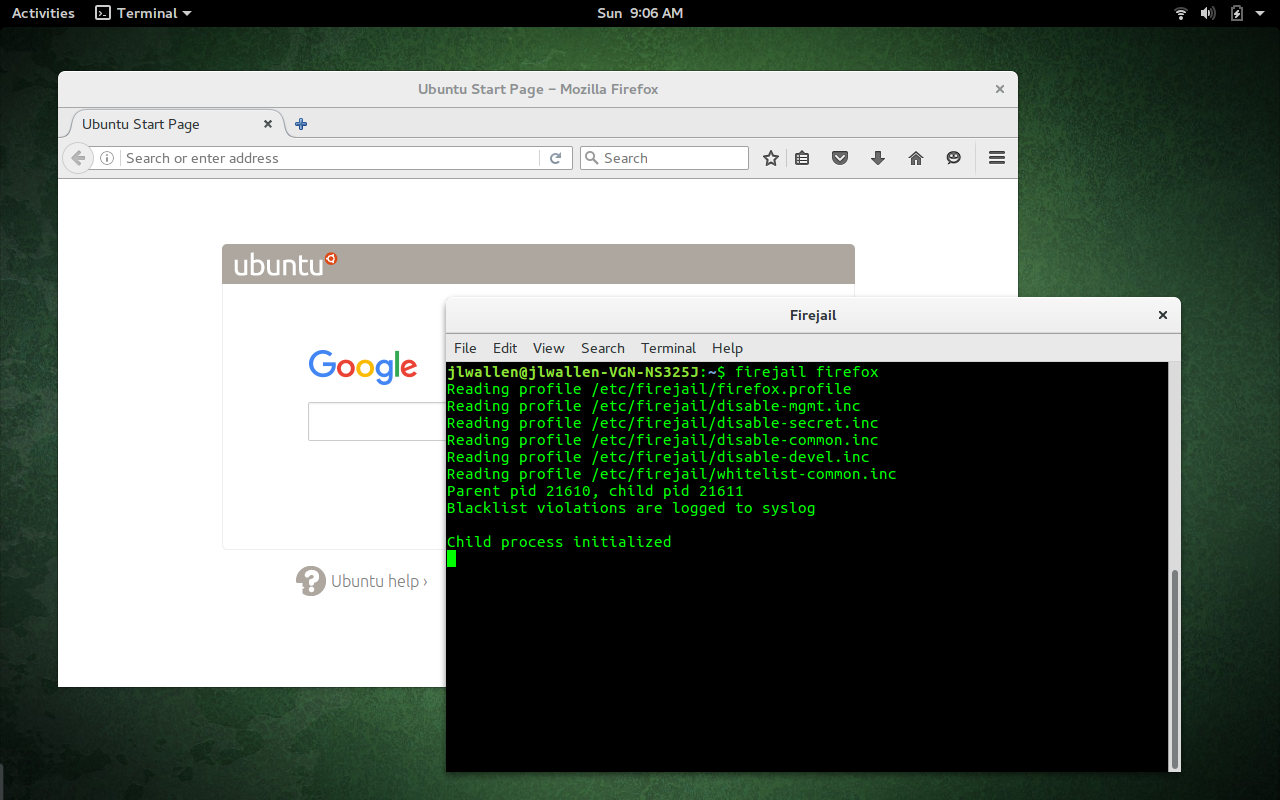
To close an application running in a Firejail, simply close it as you normally would.
Firejail works with profiles. It includes profiles for a number of popular applications, as well as a very restrictive default profile. If Firejail does not find a profile for an executed command, it will run the application with the default profile. You can create a custom profile for an application with the following steps:
-
Open up a terminal window
-
Issue the command mkdir -p ~/.config/firejail
-
Change into the newly created directory
-
Copy the default profile into the newly created directory with the command cp /etc/firejail/generic.profile ~/.config/firejail/APPNAME.profile (where APPNAME is the name of the app to be used)
-
Edit the newly created profile to suit your needs
The generic profile looks like this:
################################ # Generic GUI application profile ################################ include /etc/firejail/disable-mgmt.inc include /etc/firejail/disable-secret.inc include /etc/firejail/disable-common.inc blacklist ${HOME}/.pki/nssdb blacklist ${HOME}/.lastpass blacklist ${HOME}/.keepassx blacklist ${HOME}/.password-store caps.drop all seccomp protocol unix,inet,inet6 netfilter noroot
Say, for example, you wanted to prevent that application from accessing your user Documents directory. To do this, you would add the following to the newly created profile:
blacklist ${HOME}/Documents
NOTE: You can also write that out with the explicit path to the directory, like so:
blacklist /home/USERNAME/Documents
where USERNAME is the actual name of the user.
Now, suppose an app needs access to a particular directory, but you want to limit it to read only access. You can enable this in the profile with the line:
read-only ${HOME}/Documents
To find out more of what you can do with the newly created profile, issue the command man firejail-profile. This will show you a complete description of what other restrictions you can apply to the new profile.
Using Firetools
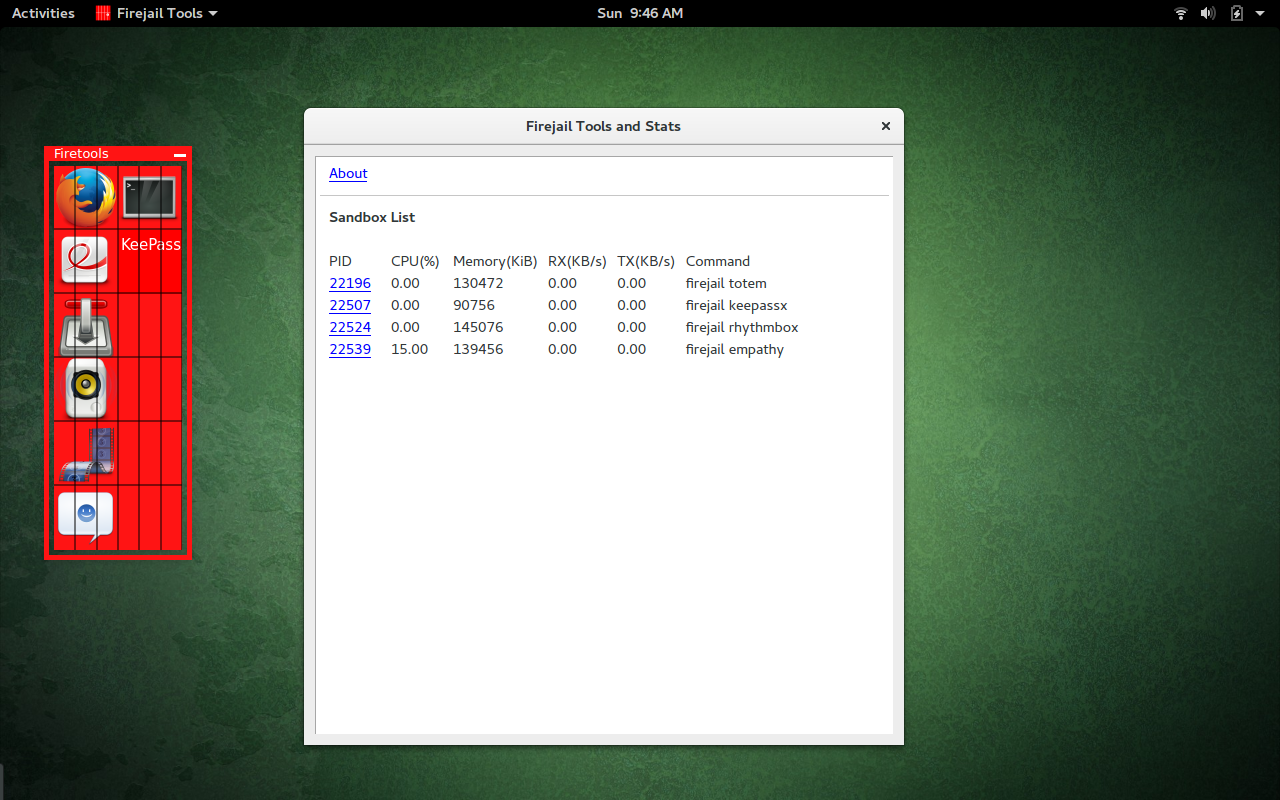
Let’s take a look at how the Firejail GUI, Firetools, works. From a terminal window, issue the command firetools & to start up the tool. You should see two things: The Firetools window and an indicator for the running app in the system tray. In GNOME 3, you’ll notice, at the bottom left corner, a slideout app that you can call up at any time to reveal access to the Firetools GUI (Figure 2).

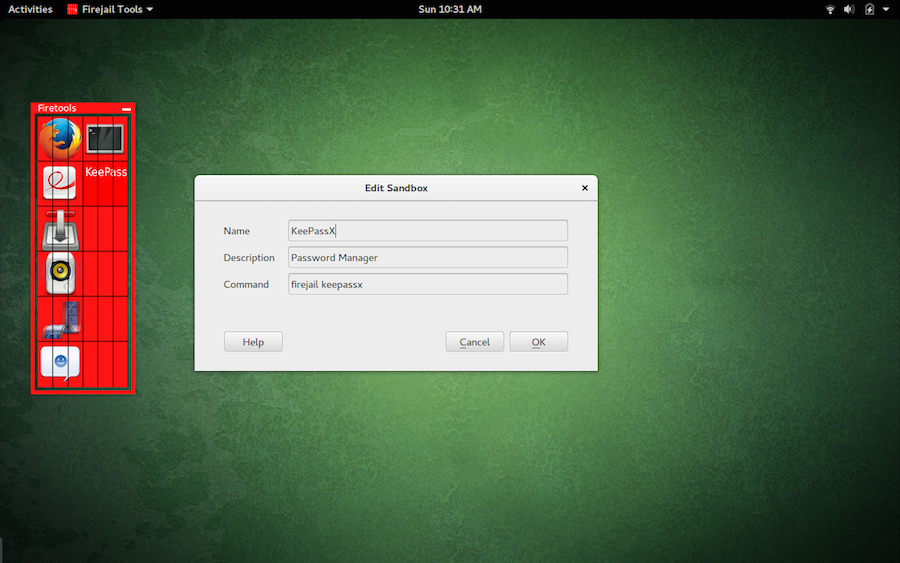
To add a new app to Firetools, right-click the GUI and click Edit. In the new window (Figure 4), fill out the details for the app. In the Command section, you must include firejail. If you want to add an entry for KeePassX, the Command section will be firejail keepassx.
A Must-Use for the Security Minded
If you want to be able to run standard apps in a sandboxed environment, using Firejail is one of the easiest ways to achieve this task. Firejail is user-friendly and ready to help prevent untrusted apps from gaining access to sensitive data on your system. Give it a try and see if it doesn’t help you find peace of mind with those third-party Linux apps.





