Wait, Linux needs antivirus and anti-malware solutions? I thought it was immune to such things. Perhaps a bit of clarification is necessary here.
First and foremost, no operating system is 100 percent immune to attack. Whether a machine is online or offline, it can fall victim to malicious code. Although Linux is less prone to such attacks than, say, Windows, there is no absolute when it comes to security. I have witnessed, first hand, Linux servers hit by rootkits that were so nasty, the only solution was to reinstall and hope the data backup was current. I’ve been a victim of a (very brief) hacker getting onto my desktop, because I accidentally left desktop sharing running (that was certainly an eye opener). The lesson? Even Linux can be vulnerable.
So why does Linux need tools to prevent viruses, malware, and rootkits? It should be obvious why every server needs protection from rootkits — because once you are hit with a rootkit, all bets are off as to whether you can recover without reinstalling the platform. It’s antivirus and anti-malware where admins start getting a bit confused.
Let me put it simply — if your server (or desktop for that matter) makes use of Samba or sshfs (or any other sharing means), those files will be opened by users running operating systems that are vulnerable. Do you really want to take the chance that your Samba share directory could be dishing out files that contain malicious code? If that should happen, your job becomes exponentially more difficult. Similarly, if that Linux machine performs as a mail server, you would be remiss to not include AV scanning (lest your users be forwarding malicious mail).
With all of that said, what are your options? Let’s take a look at a few tools, offered for the Linux platform, that do a good job of protecting you (and your users) from viruses, malware, and rootkits.
ClamAV
Without a doubt, ClamAV is the most popular option for keeping viruses off of your Linux machines and out of your shared directories. There are a few reasons why ClamAV is so popular among the Linux crowd. First, it’s open source, which in and of itself is a big win. Second, it’s very effective in finding trojans, viruses, malware, and other threats. ClamAV features a multi-threaded scanner daemon that is perfectly suited for mail servers and on-demand scanning.
ClamAV can be run from command line or it with the ClamTK GUI. Both tools are easy to use and very dependable. Installing ClamAV is simple.
For Debian-based systems:
sudo apt install clamav
For RHEL/CentOS systems:
sudo yum install epel-release sudo yum install clamav
For Fedora-based systems:
sudo dnf install clamav
For SUSE-based systems:
sudo zypper in clamav
If you’re running a Debian-based desktop, you can install ClamTK (the GUI) with the command:
sudo apt install clamtk
There are also third-party tools that can be added (to include support for the likes of MTA, POP3, Web & FTP, Filesys, MUA, Bindings, and more).
Upon installation, the first thing you’ll want to do is update the signatures with the command sudo freshclam. Once that completes, you can scan a directory with the command:
clamscan -r -i DIRECTORY
where DIRECTORY is the location to scan. The -r option means to recursively scan and the -i options means to only print out infected files. If you work with the GUI, it’s even easier. From the GUI you can run a scan and, should ClamAV find anything, act on it (Figure 1).
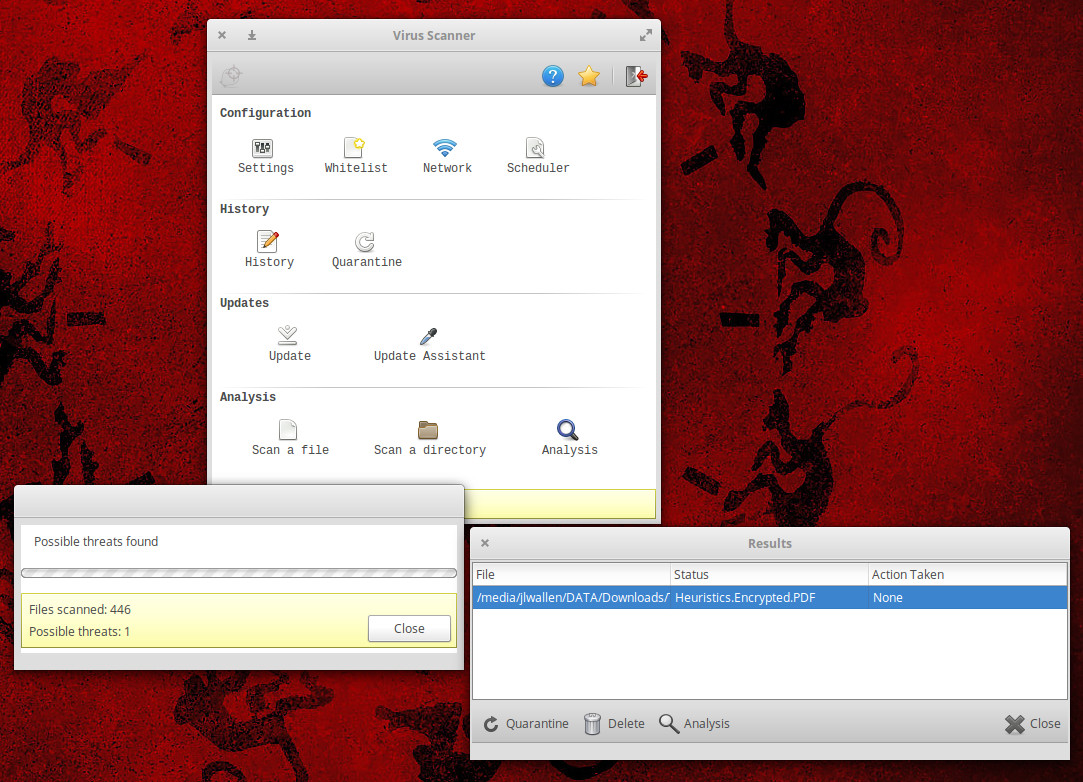
The one caveat to ClamAV is that it does not include real-time scanning. In fact, if you’re not using the ClamTK GUI, then to create a scheduled scan, you must make use of crontab. With the ClamTK GUI, you can only set up a schedule for your user home directory.
Sophos
If you’re looking for a non-open source solution from a company that’s been in the antivirus sector for quite some time, Sophos offers a free Linux scanner that does an outstanding job. This particular solution does on-access and on-demand scans for viruses, trojans, and malware. To prevent your Linux machine from becoming a distribution point for malicious software, Sophos Antivirus for Linux detects, blocks, and removes Windows, Mac, and Android malware. What makes Sophos stand above ClamAV is the inclusion of a real-time scanner. For desktops that share a lot of files, that is a deal maker.
Once you’ve agreed to the Sophos license (and entered a bit of information), you can download the distribution-agnostic installer, extract the file, and install with the command sudo sh install.sh. During the installation (Figure 2), you’ll be asked if you want to enable on-access scanning (real-time).
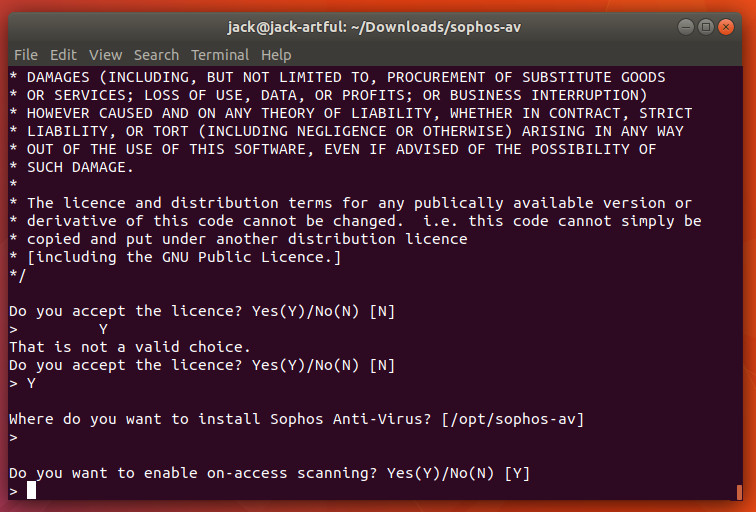
You will also be asked what type of auto-updating to be used for virus definitions. You can choose from Sophos servers, your own servers, or none. You can also choose to install the free or the supported version of Sophos as well as configure a proxy (if necessary).
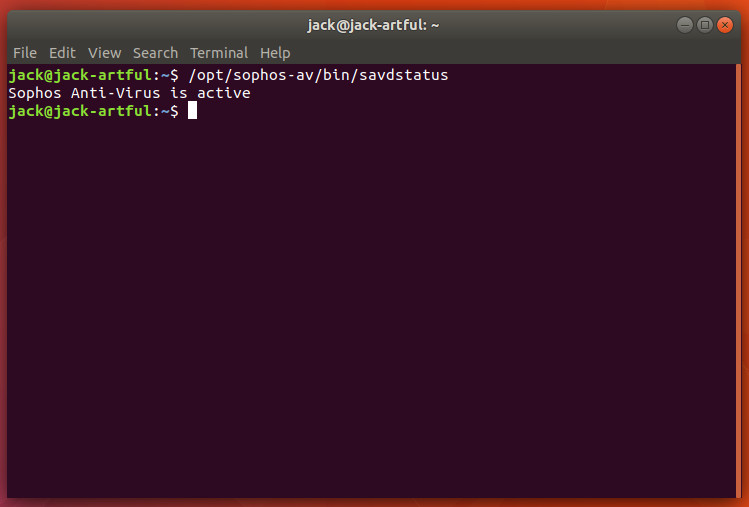
When the installation completes, Sophos is running and protecting your machine in real time. There is no GUI for Sophos, so you’re restricted to the command line. You can check to see if Sophos is running with the command:
/opt/sophos-av/bin/savdstatus
Upon issuing the command, you should see Sophos Anti-Virus is active (Figure 3).
If you want to run an on-demand scan, it is as simple as:
savscan DIRECTORY
Where DIRECTORY is the directory to be scanned.
chkrootkit and rkhunter
No tool is more important to the security of your Linux server than either chkrootkit or rkhunter. These particular tools check for the likes of:
-
System binaries for rootkit modification
-
If the interface is in promiscuous mode
-
lastlog deletions
-
wtmp deletions
-
Signs of LKM trojans
-
Quick and dirty strings replacement
-
utmp deletions
The chkrootkit tool can be installed on Debian-based systems with the following command:
sudo apt install chkrootkit
The rkhunter tool can be installed on CentOS-like systems with the commands:
sudo yum install epel-release sudo yum install rkhunter
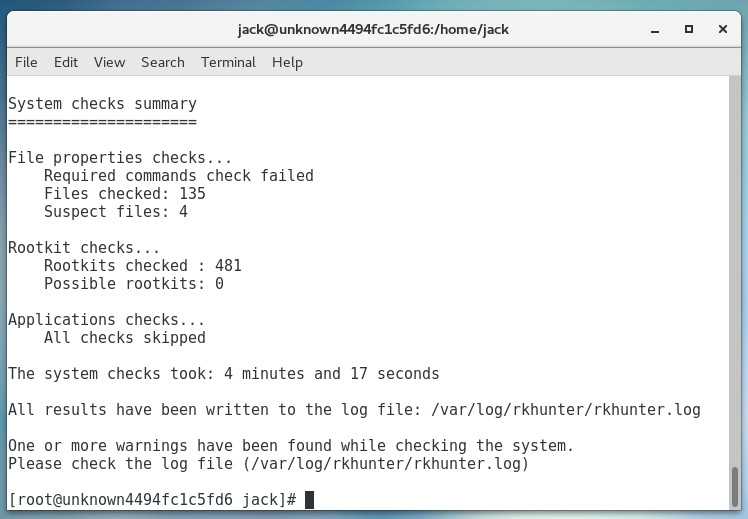
Once installed, the usage is very simple: Issue either sudo chkrootkit or sudo rkhunter -c. Both commands will dive into the system and check for any known rootkits. During the rkhunter scan, you will have to press Enter on your keyboard (when prompted), as it runs through the different stages of the check. When the scan completes, both tools will report back their findings (Figure 4).
Stay safe
There are plenty more options out there, but these four tools should go a long way to keep you safe. Whether you only need a command line antivirus/malware/trojan scanner, a GUI, or a tool to hunt for rootkits, you’re covered. Just don’t fall into the trap of thinking that, because you’re using Linux, you are perfectly safe…even without protection.
Learn more about Linux through the free “Introduction to Linux” course from The Linux Foundation and edX.





