Unlike servers or networking equipment, which are typically hacked through isolated access points and exist in sandboxed and supervised environments, IoT devices are more vulnerable to malevolent threat actors.
The underlying risk to a larger network
If one device is compromised, it’s next to impossible for a vendor to issue an OTA and update millions of devices. An insecure device in a network is enough to put the whole network and the devices connected to it in jeopardy: servers, smartphones, and desktops in addition to IoT devices, letting a single device to compromise confidential data from bank and health information.
Vendors are startups and SMBs
IoT companies are mostly startups and SMBs and have enough fund only to back their R&D and marketing team. They don’t have the funds to hire an army of security experts and ethical hackers to ensure secure deployments. As an alternative, they bake security features in IoT’s software environment that is often outsourced to a enterprises app development company in Asia Pacific to cut cost and boost margin in a hyper competitive market. Many of the IoT devices on today’s shelves are by necessity inexpensive to manufacture, which means companies are less likely to spend high dollar on security throughout the development process.
The security Surprises
I do laundry every Sunday afternoon. One fine day my smart washing machine did not work. I unlocked my iPhone and tried to reset it; it did not. The very moment the machine sent me a notification “We hacked your machine and it will only work with our detergent now”. So I ordered a year’s supply of the detergent even when I did not want to.
This did not happen with me. But it might.
A few months ago, a group of naysayers hijacked a smart refrigerator to make it show pornographic spam while making ice cubes. Baby monitors can be turned into eavesdropping devices. CIA tools can hack IoT devices, such as Samsung SmartTVs, and turn them into a bugging device.
Gartner, Inc. forecasts that 6.4 billion connected things are in use worldwide in 2016 and will reach 20.8 billion by 2020.
The two categories of security threats
Threats to IoT can be divided into two categories. First, devices are taken over to do something they are not intended to do, like a home surveillance system that uploads photos to Instagram every minute
Second, devices can be commandeered to do precisely what they are supposed to do but with a catch. A hijacked Nest will set room temperature beyond human tolerance limit.
Vendors are doing their bit from putting end point security suites to data encryption. The question is, is this enough?
1. The everyday security
Defending and fortifying the network connecting IoT devices to back-end systems over the internet, IoT network security, owing to lack of common standards and protocols unlike traditional network security devices poses significant problems and larger difficulties.
An everyday endpoint security suite with antivirus, antispyware and firewalls and intrusion prevention and detection systems shall help.
2. Passwords, biometrics and beyond
Letting users to authenticate IoT devices from a username and password combination to more sophisticated verification mechanisms such as two-way authentication, digital certificates, retina and fingerprint scanners.
The catch is IoT authentication scenarios are not man-to-machine but machine-to-machine. Biometric methods can only stop a person from accessing the IoT device, not another machine or ‘talking’ smart device.
3. Encrypting data and communication
Encrypting data stored in an IoT device, on cloud and in transit will ensure that an unsolicited device or human can’t get access to it. Standard cryptographic algorithms ensure data integrity and avert data sniffing by hackers.
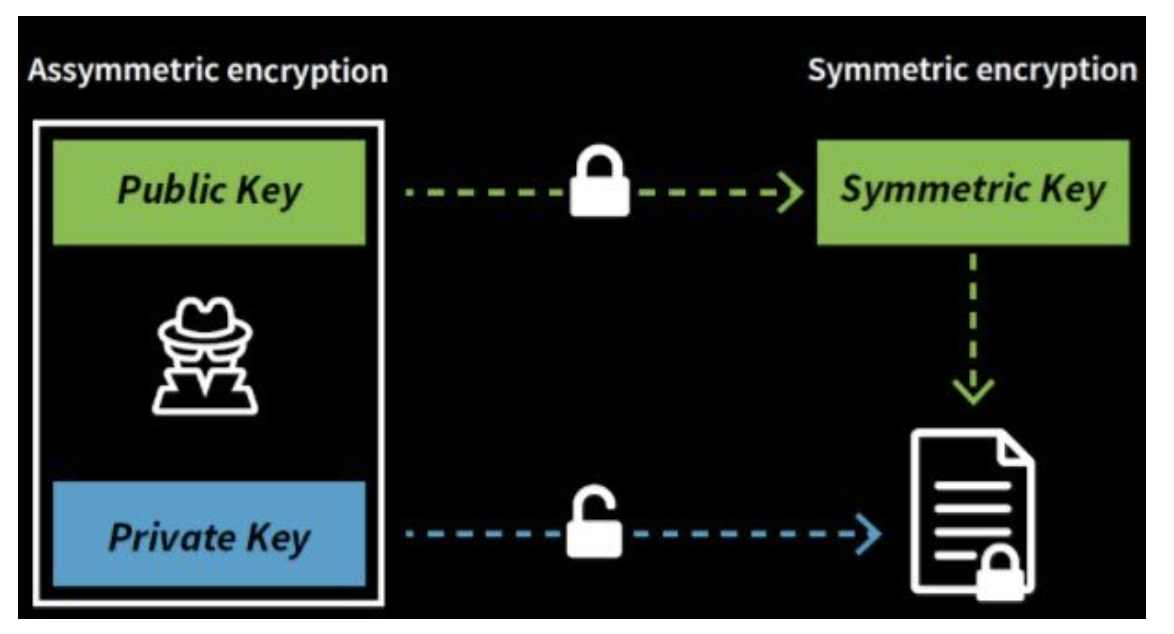
Again, IoT fragmentation confines standard encryption methods and procedures in IoT implementation.
4. Public Key Infrastructure
Offering comprehensive cryptographic key and life-cycle capabilities, X.509 digital certificate and providing public/private key generation, delivery, supervision, and cancelation.
The specification of low-cost IoT devices may confine or avert possibility to employ Public Key Infrastructure.
Vendors for the sake of security must start including Digital certificates hardcoded to IoT devices at the time of distribution and letting an authorized third party IoT device activate it at the time of authentication. DigiCert, and Gemalto can help.
5. AI and Machine Learning
Gathering, combining, monitoring, and standardizing data from various IoT devices in a system and offering disallowed reporting and warning on specific events, particularly when they fall outside the purview of established policies.
Artificial intelligence assisted data mining will give way to more analytical modeling and glitch detection, but these abilities are still evolving.
IoT security analytics will gradually be needed to sense IoT-specific attacks and intrusions that are not recognized by old-school intrusion prevention system like an end point security suite.
6. API Security
The data to and from IoT devices must be authenticated before acquiring any actionable value. The data can be from a database, and mobile apps using familiar REST-based APIs.
API security will ensure only approved devices, 3rd party vendors, and mobile application are interacting with APIs, perceiving upcoming threats and attacks against particular APIs, defending the integrity of data in transit.
Will my washing machine ask for a ransom?
The ongoing evolution of IoT-specific security threats will certainly force innovation in this space. Newer IoT-specific security technologies will appear soon.
It’s authoritative for digital businesses today to balance the business goals that IoT-connected products can bring with the recognition that the smart devices have turn out to be a striking attack plane for pranksters, hackers and even cybercriminals looking to create nuisance, disruption and gain access to sensitive data.





